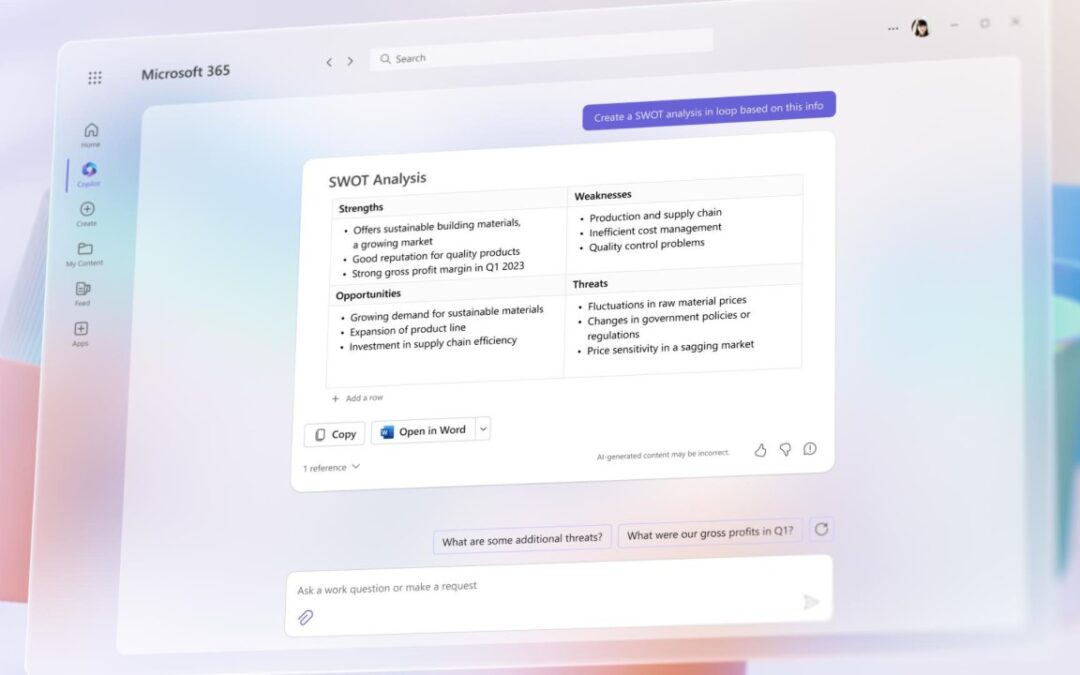
by admin | Mar 4, 2024 | Blog, Cloud, Cloud Guidance, Cyber security, Security
Does Microsoft 365 Copilot have business potential? Microsoft 365 Copilot represents a significant advancement in AI-driven productivity. It offers businesses benefits aimed at streamlining workflows, enhancing collaboration and maximizing efficiency. But there’s a...

by admin | Mar 4, 2024 | Blog, Cloud, Cloud Guidance, Cyber security, Security, VoIP
https://www.ncsc.gov.uk/blog-post/protecting-pbx-from-cyber-attacks Safeguarding Your VoIP Phone System with Cloud Heroes When we think of cybercrime and the many threats that face business, we mainly think about networks, servers, data and so on. Rarely do we think...

by admin | Jan 29, 2024 | Blog, Cloud, Cloud Guidance, Cyber security, Security
AI likely to increase global ransomware threat in 2024 The National Cyber Security Centre estimates a marked increase in ransomware thanks to the rise of AI and its increased use for crime. Their recent report, ‘The near-term impact of AI on the cyber threat’ shares a...

by admin | Jan 4, 2024 | Blog, Cloud, Cloud Guidance, Cyber security, Security
Hybrid cloud benefits and use cases One size rarely fits all in business, especially digital businesses. That’s why hybrid cloud is gaining such huge traction. But what is hybrid cloud? What benefits does it bring and to whom? What is hybrid cloud? A hybrid cloud is a...

by admin | Oct 25, 2023 | Blog, Cyber security, Security
Is your company security strategy ready for 2024? You can always depend on criminals to try to prey on the vulnerable when times are tough. Just because you’re a business, doesn’t mean you’re not regarded as vulnerable. Businesses are a prime target for cyber attacks...






